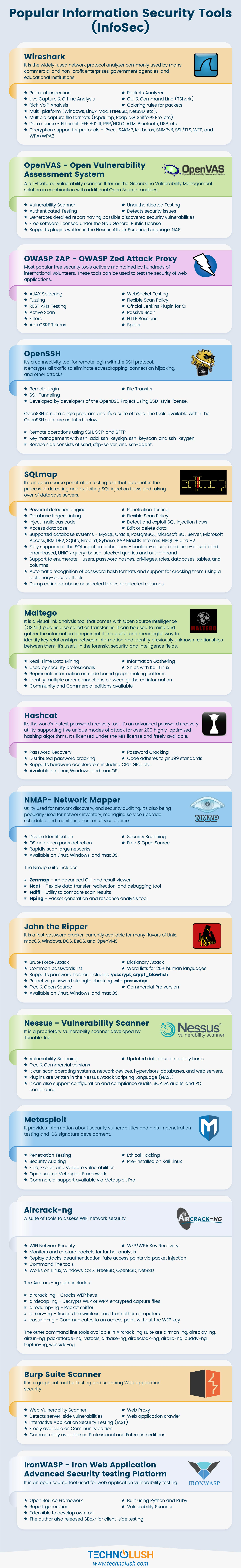
The information security tools are widely used by information security professionals and server admins. Most of these tools are used for security testing and network analyzing to find out application vulnerability.
The popular information security tools are as listed below.
Wireshark
It is the widely-used network protocol analyzer commonly used by many commercial and non-profit enterprises, government agencies, and educational institutions.
- Protocol Inspection
- Packets Analyzer
- Live Capture & Offline Analysis
- GUI & Command Line (TShark)
- Rich VoIP Analysis
- Coloring rules for packets
- Multi-platform (Windows, Linux, Mac, FreeBSD, NetBSD, etc).
- Multiple capture file formats (tcpdump, Pcap NG, Sniffer® Pro, etc)
- Data source - Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, etc.
- Decryption support for protocols - IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2
OpenVAS
A full-featured vulnerability scanner. It forms the Greenbone Vulnerability Management solution in combination with additional Open Source modules.
- Vulnerability Scanner
- Unauthenticated Testing
- Authenticated Testing
- Detects security issues
- Generates detailed report having possible discovered security vulnerabilities
- Free software, licensed under the GNU General Public License
- Supports plugins written in the Nessus Attack Scripting Language, NAS
OWASP ZAP - OWASP Zed Attack Proxy
Most popular free security tools actively maintained by hundreds of international volunteers. These tools can be used to test the security of web applications.
- AJAX Spidering
- WebSocket Testing
- Fuzzing
- Flexible Scan Policy
- REST APIs Testing
- Official Jenkins Plugin for CI
- Active Scan
- Passive Scan
- Filters
- HTTP Sessions
- Anti CSRF Tokens
- Spider
OpenSSH
It's a connectivity tool for remote login with the SSH protocol. It encrypts all traffic to eliminate eavesdropping, connection hijacking, and other attacks.
- Remote Login
- File Transfer
- SSH Tunneling
- Developed by developers of the OpenBSD Project using BSD-style license
OpenSSH is not a single program and it's a suite of tools. The tools available within the OpenSSH suite are as listed below.
- Remote operations using SSH, SCP, and SFTP
- Key management with ssh-add, ssh-keysign, ssh-keyscan, and ssh-keygen
- Service side consists of sshd, sftp-server, and ssh-agent
SQLmap
It's an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers.
- Powerful detection engine
- Penetration Testing
- Database fingerprinting
- Flexible Scan Policy
- Inject malicious code
- Detect and exploit SQL injection flaws
- Access database
- Edit or delete data
- Supported database systems - MySQL, Oracle, PostgreSQL, Microsoft SQL Server, Microsoft Access, IBM DB2, SQLite, Firebird, Sybase, SAP MaxDB, Informix, HSQLDB and H2
- Fully supports all the SQL injection techniques - boolean-based blind, time-based blind, error-based, UNION query-based, stacked queries and out-of-band
- Support to enumerate - users, password hashes, privileges, roles, databases, tables, and columns
- Automatic recognition of password hash formats and support for cracking them using a dictionary-based attack
- Dump entire database or selected tables or selected columns
Maltego
It is a visual link analysis tool that comes with Open Source Intelligence(OSINT) plugins also called as transforms. It can be used to mine and gather the information to represent it in a useful and meaningful way to identify key relationships between information and identify previously unknown relationships between them. It's useful in the forensic, security, and intelligence fields.
- Real-Time Data Mining
- Information Gathering
- Used by security professionals
- Ships with Kali Linux
- Represents information on node-based graph making patterns
- Identify multiple order connections between gathered information
- Community and Commercial editions available
Hashcat
It's the world's fastest password recovery tool. It's an advanced password recovery utility, supporting five unique modes of attack for over 200 highly-optimized hashing algorithms. It's licensed under the MIT license and freely available.
- Password Recovery
- Password Cracking
- Distributed password cracking
- Code adheres to gnu99 standards
- Supports hardware accelerators including CPU, GPU, etc
- Available on Linux, Windows, and macOS
NMAP - Network Mapper
Utility used for network discovery, and security auditing. It's also being popularly used for network inventory, managing service upgrade schedules, and monitoring host or service uptime.
- Device Identification
- Security Scanning
- OS and open ports detection
- Free & Open Source
- Rapidly scan large networks
- Available on Linux, Windows, and macOS
The Nmap suite includes
- Zenmap - An advanced GUI and result viewer
- Ncat - Flexible data transfer, redirection, and debugging tool
- Ndiff - Utility to compare scan results
- Nping - Packet generation and response analysis tool
John the Ripper
It is a fast password cracker, currently available for many flavors of Unix, macOS, Windows, DOS, BeOS, and OpenVMS.
- Brute Force Attack
- Dictionary Attack
- Common passwords list
- Word lists for 20+ human languages
- Supports password hashes including yescrypt, crypt_blowfish
- Proactive password strength checking with passwdqc
- Free & Open Source
- Commercial Pro version
- Available on Linux, Windows, and macOS
Nessus - Vulnerability Scanner
It is a proprietary Vulnerability scanner developed by Tenable, Inc.
- Vulnerability Scanning
- Updated database on a daily basis
- Free & Commercial versions
- It can scan operating systems, network devices, hypervisors, databases, and web servers
- Plugins are written in the Nessus Attack Scripting Language (NASL)
- It can also support configuration and compliance audits, SCADA audits, and PCI compliance
Metasploit
It provides information about security vulnerabilities and aids in penetration testing and IDS signature development.
- Penetration Testing
- Ethical Hacking
- Security Auditing
- Pre-installed on Kali Linux
- Find, Exploit, and Validate vulnerabilities
- Open source Metasploit Framework
- Commercial support available via Metasploit Pro
Aircrack-ng
A suite of tools to assess WIFI network security.
- WIFI Network Security
- WEP/WPA Key Recovery
- Monitors and capture packets for further analysis
- Replay attacks, deauthentication, fake access points via packet injection
- Command line tools
- Works on Linux, Windows, OS X, FreeBSD, OpenBSD, NetBSD
The Aircrack-ng suite includes
- aircrack-ng - Cracks WEP keys
- airdecap-ng - Decrypts WEP or WPA encrypted capture files
- airodump-ng - Packet sniffer
- airserv-ng - Access the wireless card from other computers
- easside-ng - Communicates to an access point, without the WEP key
The other command line tools available in Aircrack-ng suite are airmon-ng, aireplay-ng, airtun-ng, packetforge-ng, ivstools, airbase-ng, airdecloak-ng, airolib-ng, buddy-ng, tkiptun-ng, wesside-ng
Burp Suite
It is a graphical tool for testing and scanning Web application security.
- Web Vulnerability Scanner
- Web Proxy
- Detects server-side vulnerabilities
- Web application crawler
- Interactive Application Security Testing (IAST)
- Freely available as Community edition
- Commercially available as Professional and Enterprise editions
IronWASP
Iron Web Application Advanced Security testing Platform - It is an open source tool used for web application vulnerability testing.
- Open Source Framework
- Built using Python and Ruby
- Report generation
- Vulnerability Scanner
- Extensible to develop own tool
- The author also released SBoxr for client-side testing
Notes: This list collectively shows the popular and commonly used information security tools. The usage of these tools solely depends on the user and there is no direct or indirect link of actual usage with this infographic.