May 03, 2019
Explains the different types of join operations that can be performed using Structured Query Language (SQL). ...
Read More
April 15, 2019
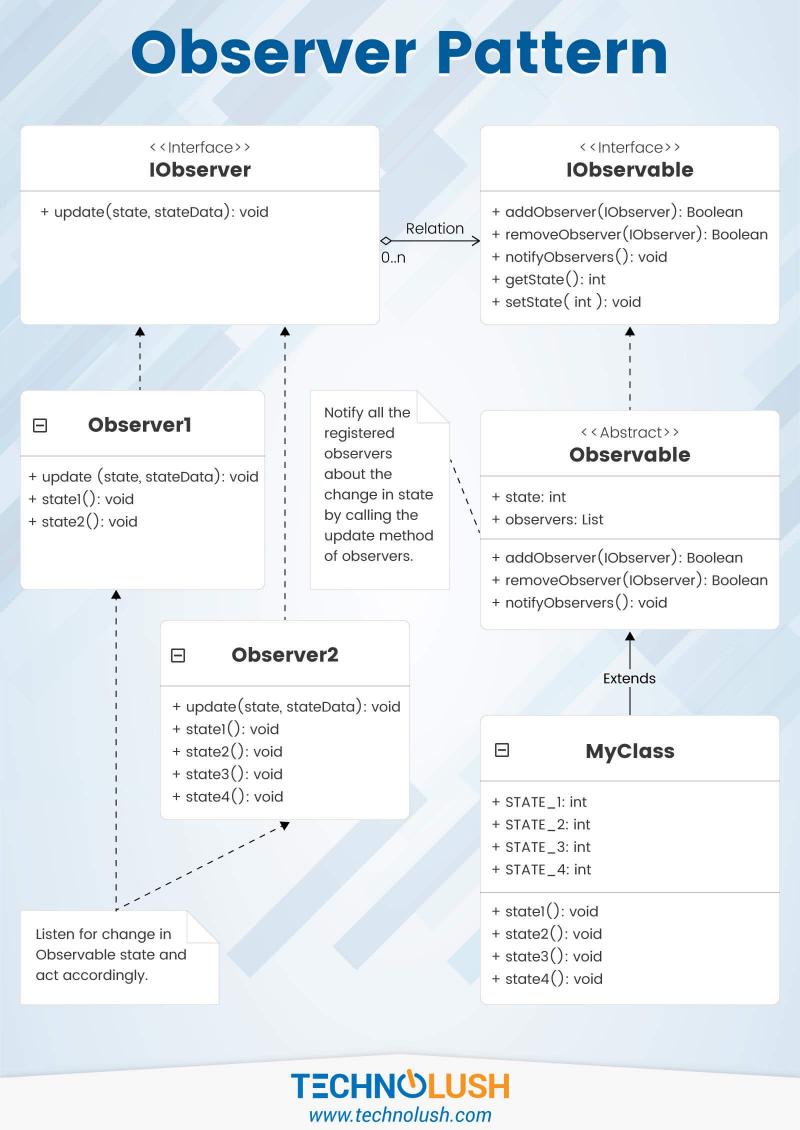
Explains the functionality of Observer Pattern to process the state change distributed by the Subject to it's registered listeners or observers. ...
Read More
April 05, 2019
List of commonly used hacking techniques by hackers. ...
Read More
March 27, 2019
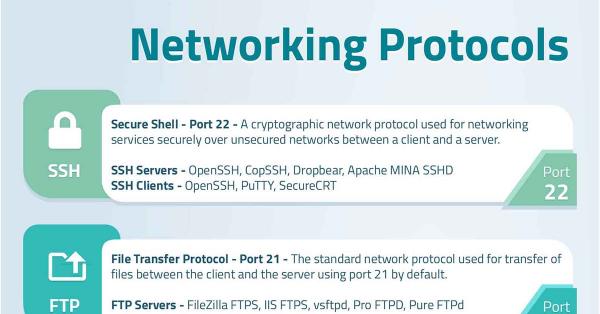
Provides a list of all the popular and standard protocols with their definition and default port where applicable. ...
Read More
March 22, 2019
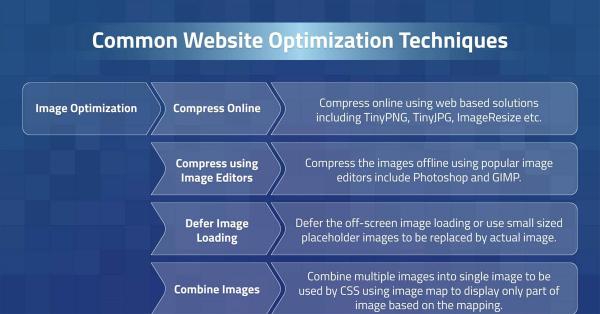
Provides a list of most common optimization techniques used to speed up the website load time resulting in faster websites. ...
Read More
March 12, 2019
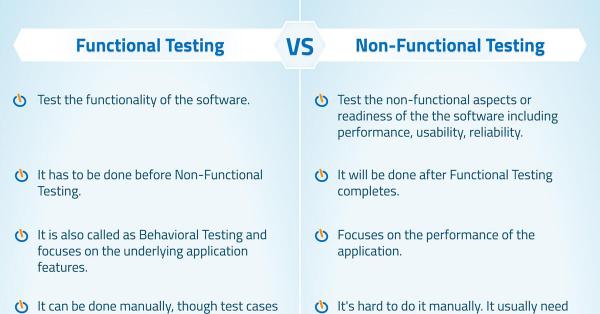
Provides a list of major differences between functional and non-functional testing. ...
Read More
March 09, 2019
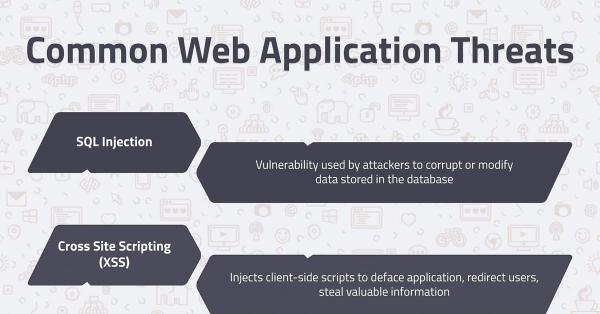
Lists the most common web application threats ...
Read More
March 08, 2019
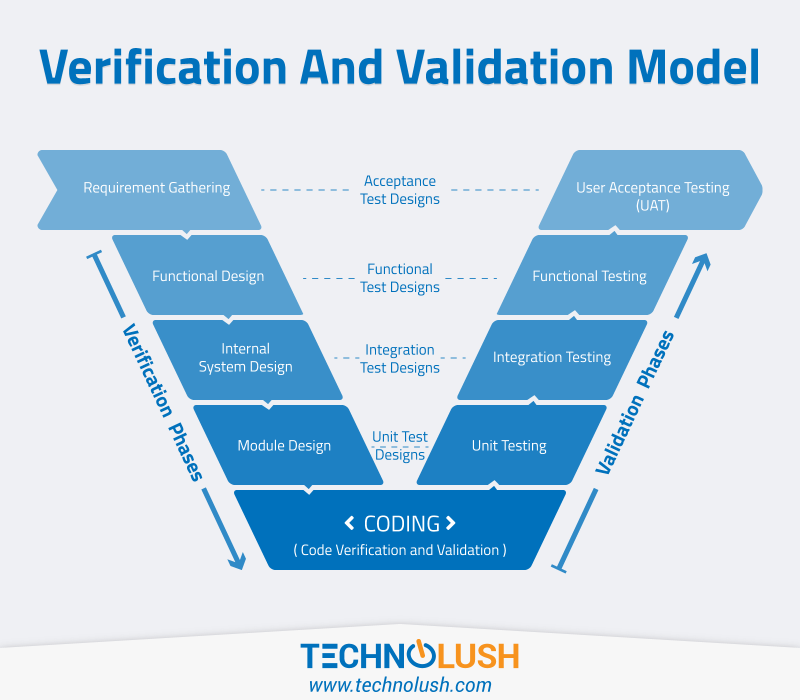
Explains the various SDLC(Software Development Life Cycle) phases involved in verification and validation model to simultaneously progress on development and testing of the underlying software. ...
Read More
March 02, 2019
List of the common mistakes done by the programmers at the beginners level. ...
Read More
February 26, 2019
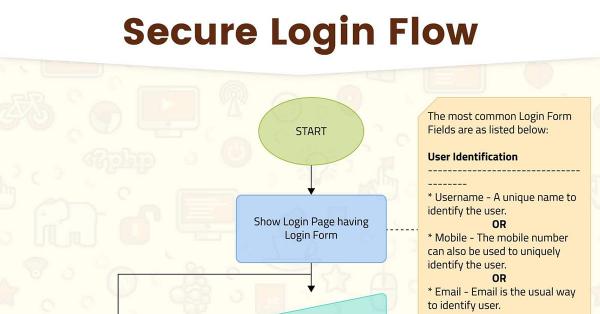
A flowchart explaining the implementation of secure login using the combination of username, email, and mobile number. ...
Read More